DrayTek Vigor 2600v does some DNS spoofing
I always wondered about an obscure behaviour observed in my home network.
Whenever I access my website using it’s plain domain name (http://phunsites.net), I’d end up with a password prompt from my DSL router.
Thinking about DNS it would be an easy asumption that there was likely to be a wrong resource record like this in my DNS zone:
@ IN A 192.0.2.1
But it turned there wasn’t – why should it anyway?
Looking further into this, I did a DNS trace. It was strinking that querying for www.phunsites.net would yield another result …
$ dig A www.phunsites.net. ; <<>> DiG 9.6.0-APPLE-P2 <<>> A www.phunsites.net. ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 24771 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 4, ADDITIONAL: 8 ;; QUESTION SECTION: ;www.phunsites.net. IN A ;; ANSWER SECTION: www.phunsites.net. 86170 IN A 82.195.224.130 ;; AUTHORITY SECTION: phunsites.net. 60583 IN NS ns1.genotec.ch. phunsites.net. 60583 IN NS ns2.genotec.ch. phunsites.net. 60583 IN NS ns3.genotec.ch. phunsites.net. 60583 IN NS ns4.genotec.ch. ;; ADDITIONAL SECTION: ns1.genotec.ch. 58593 IN A 82.195.224.5 ns1.genotec.ch. 58593 IN AAAA 2001:1b50::82:195:224:5 ns2.genotec.ch. 58593 IN A 82.195.225.5 ns2.genotec.ch. 58593 IN AAAA 2001:1b50::82:195:225:5 ns3.genotec.ch. 58593 IN A 82.195.235.37 ns3.genotec.ch. 58593 IN AAAA 2001:1b50::2:82:195:235:37 ns4.genotec.ch. 58593 IN A 82.195.235.69 ns4.genotec.ch. 58593 IN AAAA 2001:1b50::3:82:195:235:69 ;; Query time: 12 msec ;; SERVER: 82.195.225.6#53(82.195.225.6) ;; WHEN: Tue Apr 5 13:43:27 2011 ;; MSG SIZE rcvd: 309
... than phunsites.net:
$ dig A phunsites.net. ; <<>> DiG 9.6.0-APPLE-P2 <<>> A phunsites.net. ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 60489 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; WARNING: Messages has 1 extra bytes at end ;; QUESTION SECTION: ;phunsites.net. IN A ;; ANSWER SECTION: phunsites.net. 60 IN A 192.0.2.1 ;; Query time: 1 msec ;; SERVER: 82.195.225.6#53(82.195.225.6) ;; WHEN: Tue Apr 5 13:43:47 2011 ;; MSG SIZE rcvd: 48
That was very bizare. As it turned out, the DrayTek Vigor does DNS proxying by default.
There's usually nothing too wrong about that, but in my case, it was pretty annoying, because the router seemed to inject it's own IP address for queries destined to its domain name.
So my intent was to remove the domain name which I had earlier configured on the router GUI. Unfortunately that was not possible. Whenever I deleted my domain name it would show up again later on in the GUI, even after a reboot.
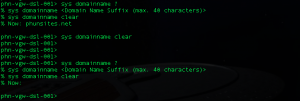
So I gave it a shot through the Telnet CLI, where I tried to remove the domain name using this command "sys domainname clear".
Checking back with dig it turned out to give me the proper DNS reply I expected earlier for qerying phunsites.net:
$ dig A phunsites.net. ; <<>> DiG 9.6.0-APPLE-P2 <<>> A phunsites.net. ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 50148 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 4, ADDITIONAL: 8 ;; QUESTION SECTION: ;phunsites.net. IN A ;; ANSWER SECTION: phunsites.net. 83205 IN A 82.195.224.130 ;; AUTHORITY SECTION: phunsites.net. 59427 IN NS ns2.genotec.ch. phunsites.net. 59427 IN NS ns1.genotec.ch. phunsites.net. 59427 IN NS ns3.genotec.ch. phunsites.net. 59427 IN NS ns4.genotec.ch. ;; ADDITIONAL SECTION: ns1.genotec.ch. 57437 IN A 82.195.224.5 ns1.genotec.ch. 57437 IN AAAA 2001:1b50::82:195:224:5 ns2.genotec.ch. 57437 IN A 82.195.225.5 ns2.genotec.ch. 57437 IN AAAA 2001:1b50::82:195:225:5 ns3.genotec.ch. 57437 IN A 82.195.235.37 ns3.genotec.ch. 57437 IN AAAA 2001:1b50::2:82:195:235:37 ns4.genotec.ch. 57437 IN A 82.195.235.69 ns4.genotec.ch. 57437 IN AAAA 2001:1b50::3:82:195:235:69 ;; Query time: 44 msec ;; SERVER: 82.195.225.6#53(82.195.225.6) ;; WHEN: Tue Apr 5 14:02:43 2011 ;; MSG SIZE rcvd: 305
So to summarize: The DrayTek Vigor injects the "domain name suffix" as configure through the "sys domainname" command into the DNS proxy.
This is very odd, as I would suppose, that it would do so only for the fully qualified domain name (FQDN), which would make perfectly sense then.
Checking into this I made a lookup for the FQDN called phn-vgw-dsl-001.phunsites.net and got this reply promptly:
$ dig A phn-vgw-dsl-001.edge.phunsites.net. ; <<>> DiG 9.6.0-APPLE-P2 <<>> A phn-vgw-dsl-001.phunsites.net. ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 19107 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; WARNING: Messages has 4 extra bytes at end ;; QUESTION SECTION: ;phn-vgw-dsl-001.phunsites.net. IN A ;; ANSWER SECTION: phn-vgw-dsl-001.phunsites.net. 60 IN A 192.0.2.1 ;; Query time: 1 msec ;; SERVER: 82.195.225.6#53(82.195.225.6) ;; WHEN: Tue Apr 5 14:11:31 2011 ;; MSG SIZE rcvd: 72
I could live with this behaviour if I think that one would perhaps prefer to set a more memorizable FQDN for the device, let's say "router.phunsites.net", which would automagically appear even if no matching DNS recource records exist.
However, it feels absolutely inappropriate for the DrayTek Vigor to inject a spoofed A resource record for the domain name suffix as well. This holds especially true when a matching resource record in the zone indeed already exists.
As a IT professional I tend to always configure all settings properly on my devices. In this case, this attitude unconvered a very odd and in my opinion erronous behaviour.
As there is no current firmware to fix this, there's only two ways to work around this: Either unconfigure the domain name as shown above through the "sys domainname clear" command or use a domain name suffix, that does not collide with a real domain name or FQDN.
After all, this is surely no big deal, but a pitfall nevertheless. As DrayTek routers are still four to five times more expensive than the usually cheap home routers I wouldn't expect to see such misbehaviour.